Ransomware is a term for malware which locks computer systems and data or “holds them hostage” against the computer user’s will and demands a penalty fine to be paid in order to unlock and use the computer system again.
Ransomware is on a major rise in 2012. Just as Citadel Reveton ransomware started deploying their path to destruction, infecting hundreds of thousands of computers in Europe, the fatal ransomware known as FBI Moneypak started making it rounds throughout North America, most notably the United States.
Related ransomware: Citadel’s Reveton malware, International Police Association
What is the FBI Moneypak ransomware virus?
FBI Moneypak is ransomware that locks computer systems, alleges the computer user has been involved in illegal activity by the FBI (downloaded or distributed copyrighted material or viewed child pornography), anddemands a penalty fine of $100 or $200 be paid to unlock the computer system within the allotted time of 72 hours by use of Moneypak cards. Moneypak is the prepaid credit cards you can purchase at Walmart or Walgreens type stores (Click to view image of Moneypak card). The FBI Moneypak ransomware virus also states on the fake FBI page that you may see jail time if a fine is not paid in time.


Web cam control

When the computer user is taken to the fake FBI drive-by-download website, a video screen, which is streamed from the users connected webcam is displayed as “recording”. If you do not have a web cam connected the video screen will appear blank and will still show as recording.
Fake phone call from Microsoft
In some reported instances, victims have received phone calls from criminals claiming to be Microsoft employees informing them their computer systems have been infected. If you receive any calls like this, keep in mind these are not Microsoft employees, and contact law enforcement depending on your geographic location. These phone calls may or may not be related to the FBI Moneypak virus but carry similarities.


Anti Malware and Antivirus software isn’t working!
The FBI Moneypak virus may cause Antivirus software to malfunction. Anti Malware and Antivirus programs can be used to scan and remove the FBI Moneypak virus but in many scenarios the infection has progressed far enough to disable removal software. There are steps around this, such as entering your system in safe mode or restoring your computer, unplugging from the internet, using the optical disk drive option, safe mode with networking, or slaving your HDD.

This Facebook user removed FBI Moneypak malware by entering Windows in “Safe Mode With Command Prompt” and performing a restore. Instructions to perform system restores using safe mode are outlined further below.

This Facebook user removed FBI Moneypak malware by entering Windows in “Safe Mode With Command Prompt” and performing a restore. Instructions to perform system restores using safe mode are outlined further below.
FBI Moneypak ransomware symptoms
■ Computer system locks
■ User is directed to a fraudulent FBI website (Image)
■ Alert message appears “Attention! Your PC is blocked due to at least one of the reasons specified below”:
■ You have been violating Copyright and related rights Law (Video, Music,Software) and illegally using or distributing copyrighted content, thus infringing Article I, Section 8, clause 8, also known as the Copyright of the Criminal Code of United States of America. If it is PCEU Virus then this is thus infringing Article 128 of the criminal code of Great Britain.
■ The ransomware details that you have been viewing or distributing prohibited pornographic content (Child Pornography/Zoofilia). Thus violating article 202 of the Criminal Code of United States of America. Article 202 of the criminal provides for deprivation of liberty for two or twelve yours.
■ Illegal access to computer data has been initiated from your PC,or you have been. Article 210 (it is 208 for PCEU Virus) of the Criminal Code provides for a fine of up to $100,000 and/or a deprivation of liberty for four to nine years.
■ Fines may only be paid within 72 hours after the infringement. As soon as 72 hours elapse, the possibility to pay the fine expires, and a criminal case is initiated against you authomatically within the next 72 hours! (Sometimes it shows you within 2 hours or 48 hours).
How to remove FBI Moneypak ransomware
Different victims of the FBI Moneypak virus will require separate removal steps due to the progress of the infection. Some users can not access the internet, nor their desktops and some still can. Since this is the case, we have outlined easy options to remove FBI Moneypak for all victims.
The suggested step to remove the FBI Moneypak is either manually or by using Malwarebytes Anti-Malware software (free or paid versions), which has been documented to scan and remove FBI Moneypak. If you can, access your computer in “safemode” (detailed below) and install Malwarebytes, then proceed to scan and remove the FBI Moneypak virus. If Anti Malware software is malfunctioning due to the infection proceed to “Safe Mode With Networking” to correctly perform a scan or install troubleshoot software. Restoring your computer is also an easy and fast solution but may not be suitable for everyone’s needs as you will need to restore your operating system to a restore point that was created before any signs of infection. Restoring your system can lead the the loss of recently installed applications as well.
The suggested step to remove the FBI Moneypak is either manually or by using Malwarebytes Anti-Malware software (free or paid versions), which has been documented to scan and remove FBI Moneypak. If you can, access your computer in “safemode” (detailed below) and install Malwarebytes, then proceed to scan and remove the FBI Moneypak virus. If Anti Malware software is malfunctioning due to the infection proceed to “Safe Mode With Networking” to correctly perform a scan or install troubleshoot software. Restoring your computer is also an easy and fast solution but may not be suitable for everyone’s needs as you will need to restore your operating system to a restore point that was created before any signs of infection. Restoring your system can lead the the loss of recently installed applications as well.
Removal Options
- Malware Removal Software – Scan and remove malware
- Manual Removal – Remove associated files
- Restore – Restore PC to a date and time before infection
- Safe Mode With Networking – Remove “ctfmon” link (or similar) and/or Scan and remove malware
- Optical CD-R Option – Scan and remove malware
- Slave Hard Disk Drive Option – Scan and remove malware
Deny Flash
The FBI Moneypak virus uses flash and in some cases disabling (denying) flash can “freeze” the FBI Moneypak virus which allows proper removal methods to be performed. Please note this is not a necessity, nor will this remove the virus. This is only an option for specific individual infections. *This may be skipped.
1. To disable (deny) flash visit:http://www.macromedia.com/support/documentation/en/flashplayer/help/help09.html

2. Select the “Deny” radio option
3. Proceed to a removal option (detailed below): Anti malware software scan and removal or system restore.
1. To disable (deny) flash visit:http://www.macromedia.com/support/documentation/en/flashplayer/help/help09.html

2. Select the “Deny” radio option
3. Proceed to a removal option (detailed below): Anti malware software scan and removal or system restore.
What happens if I select Deny?
If you select Deny, the application does not have access to your camera or your microphone. The application will continue running, but may not function as intended. Alternately, the application may inform you that it can’t continue unless you allow access, in which case you can either allow access or close the application.
1. Malware Removal Software
Not many malware removal programs are up to date with new ransomware. Your safest bet is with Malwarebytes, they provide a free or paid version and have been involved in many discussions surrounding the FBI Moneypak ransomware virus. Try Malwarebytes, the Leader in Malware Removal.

Other software recommendations
AVG has recently been documented to scan and remove FBI Moneypak. They offer a free and paid version. Please select one from the links below that suites your needs.
1. AVG Anti-Virus 2012 – 20% off
2. AVG Anti-Virus 2012 Free Edition

1. AVG Anti-Virus 2012 – 20% off
2. AVG Anti-Virus 2012 Free Edition
2. Manual Removal
It’s actually really easy to remove this virus in Windows without a restore (restore options below). Then again, if this option does not help you locate the malicious files, skip it. We are going to enter your computers App Data which is a hidden file. To learn how to show hidden files click here.
1. Open Windows Start Menu and type %appdata% into the search field, press Enter.
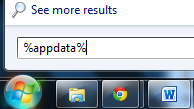
2. Navigate to: Microsoft\Windows\Start Menu\Programs\Startup
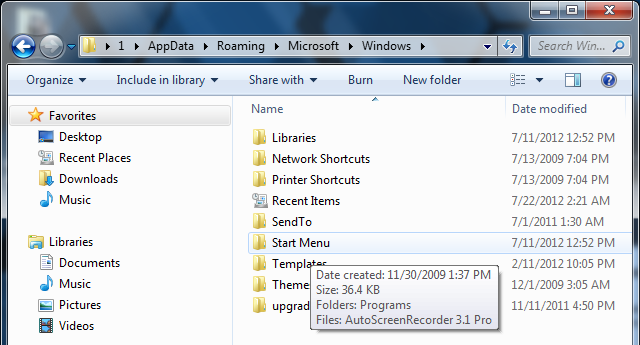
3. Remove ctfmon (ctfmon.lnk if in dos) – this is what’s calling the virus on startup
1. Open Windows Start Menu and type %appdata% into the search field, press Enter.

2. Navigate to: Microsoft\Windows\Start Menu\Programs\Startup

3. Remove ctfmon (ctfmon.lnk if in dos) – this is what’s calling the virus on startup
4. Open Windows Start Menu and type %userprofile% into the search field and press enter.

5. Navigate to: Appdata\Local\Temp
6. Remove rool0_pk.exe
7.Remove [random].mof file
8. Remove V.class

5. Navigate to: Appdata\Local\Temp
6. Remove rool0_pk.exe
7.Remove [random].mof file
8. Remove V.class
The virus can have names other than “rool0_pk.exe” but it should appear similar, there may also be 2 files, 1 being a .mof. Removing the .exe file will fix FBI Moneypak. The class file uses a java vulnerability to install the virus, removal of V.class is done for safe measure.
All FBI Moneypak files:
The files listed above are what causes FBI Moneypak to function. To ensure FBI Moneypak is completely removed via manually, please delete all given files. Keep in mind, [random] can be any sequence of numbers or letters.
Kill ROGUE_NAME processes:
Access Windows Task Manager (Ctrl+Alt+Delete) and kill the rogue FBI Moneypak process. Please note the infection will have a random name for the process [random] which may contain a sequence of numbers and letters (ie: USYHEY347H372.exe).
Remove Registry Values
To access Window’s Registry Editor type regedit into the Windows Start Menu text field and press Enter.


3. Restore – Recover Computer
Below we detail 3 different instructions to restore or recover a common Window’s computer.
To learn more about Windows System Restore for Vista, XP, and 7 please click here.
Windows Start Menu rstrui.exe Restore
1. Access Windows Start menu
2. Type rstrui.exe into the search field and press Enter
3. Follow instructions in Window’s Restore Wizard
2. Type rstrui.exe into the search field and press Enter
3. Follow instructions in Window’s Restore Wizard
Start Menu Restore
1. Access Windows Start menu and click All Programs.
2. Click and open Accessories, click System Tools, and then click System Restore.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
3. Follow the simple instructions to Restore your computer to a date and time before infection.
2. Click and open Accessories, click System Tools, and then click System Restore.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
3. Follow the simple instructions to Restore your computer to a date and time before infection.
Safe Mode With Command Prompt Restore
If you can not access Window’s desktop, this is the suggested step. If it is difficult to start windows in safe mode; if Windows’s brings up a black screen, with “safe mode” in the four corners – Move your cursor to the lower left corner, where the Search box is usually visible in Windows Start Menu and it will come up, including the “Run” box.
1. Restart/reboot your computer system. Unplug if necessary.
2. Enter your computer in “safe mode with command prompt”. To properly enter safe mode, repeatedly press F8 upon the opening of the boot menu.
2. Enter your computer in “safe mode with command prompt”. To properly enter safe mode, repeatedly press F8 upon the opening of the boot menu.
3. Once the Command Prompt appears you only have few seconds to type “explorer” and hit Enter. If you fail to do so within 2-3 seconds, the FBI MoneyPak ransomware virus will not allow you to type anymore.
4. Once Windows Explorer shows up browse to:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
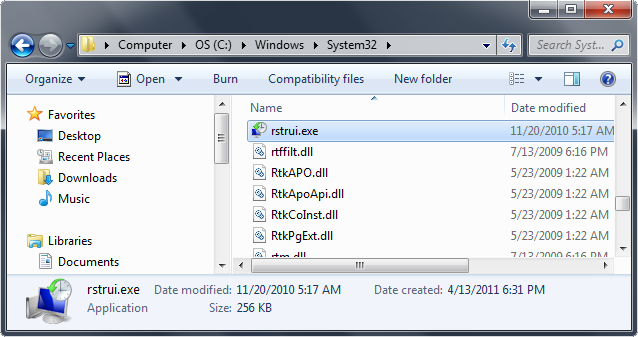
5. Follow all steps to restore or recover your computer system to an earlier time and date (restore point), before infection.
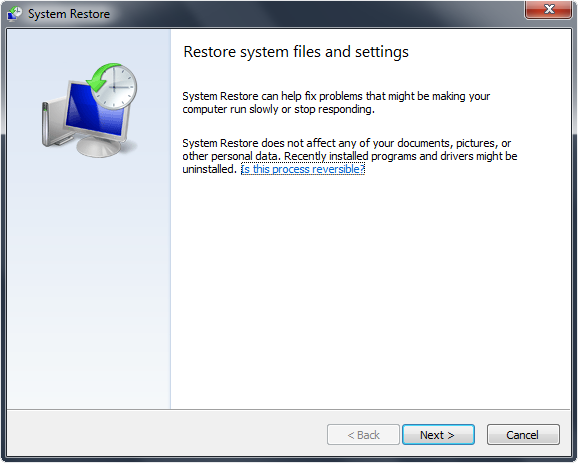
More Information Regarding Windows System Restore:
http://botcrawl.com/how-to-restore-microsoft-windows-vista-microsoft-windows-xp-and-microsoft-windows-7/
http://windows.microsoft.com/en-US/windows-vista/System-Restore-frequently-asked-questions
http://botcrawl.com/how-to-restore-microsoft-windows-vista-microsoft-windows-xp-and-microsoft-windows-7/
http://windows.microsoft.com/en-US/windows-vista/System-Restore-frequently-asked-questions
4. Safe Mode With Networking
For users needing access to the Internet or the network they’re connected to. This mode is helpful for when you need to be in Safe Mode to troubleshoot but also need access to the Internet for updates, drivers, removal software, or other files to help troubleshoot your issue.
- This mode will also bypass any issues where Antivirus or Anti Malare applications have been affected/malfunctioning because of the FBI Moneypak infection’s progression.
The plan with this option is to enter your computer in “safe mode with network” and install anti-malware software. Proceed to scan, and remove malicious files.
1. Reboot your computer in “Safe Mode with Networking”. As the computer is booting tap the “F8 key” continuously to reach the correct menu.Use your keyboard to navigate to “Safe Mode with Networking” and press Enter. Shown below.

The screen may appear black with the words “safe mode” in all four corners. Click your mouse where windows start menu is to bring up necessary browsing.

There are a few different things you can do…
This seems to be an easy step in removing the FBI virus for many users. If you are interested in learning about ctfmon.exe please click here.
Now, move on to the next steps (which is not a necessity if you removed the file above).
2. If you can easily access the internet to install removal software do so, otherwise launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.
3. It is now recommended to download Malwarebytes (free or paid version) and run a full system scan to remove FBI Moneypak malware from your computer if you do not have this application on your system.
5. Optical CD-R Option
This option was suggested by a reader and can be used in instances where internet connection is possible (even safe mode with networking).
- Place a blank CD-R into your CDROM drive
- Download Microsoft Defender onto the blank CD-R
- Restart your computer and boot from CD
“You may need an old school keyboard (not the USB, but the PC connector type) since the virus delays the USB startup. The Defender will clean your PC in totality. This virus is somehow complex, but is no match for Windows Defender. After the scan is complete, run again a full scan without a restart.”
6. Slave Hard Disk Drive Option
If you are having complications with Anti-Malware software a suggestion would be to slave your HDD, then proceed to scan. You will need a second operating computer and tools to remove your hard drive. *Please note this may be difficult for some users and there are other options to scan your hard drive during complications.
- Remove the hard disk drive from your computer.
- On the circuit board side of your HDD set the drive to “slave”.
- Connect the slave drive to an unaffected computer.
- Scan the slave drive, and proceed to remove any malware on the drive. Make sure to scan each user account.
- Reconnect the HDD to your original computer.





4 comments:
This is really good explanation and Firstly know the symptoms of FBI virus then proceed.
virus disturbs computer very much and free antivirus download is effective way to remove them.
Great post thanks
Thanks for sharing such informative post! However, I have found some additional FBI ransomware removal steps on other sites. Are these steps not enough? Why they have additional steps?
Post a Comment